Multiple user reports have surfaced warning that the latest version of WordPress is triggering trojan alerts and at least one person reported that a web host locked down a website because of the file. What really happened turned into a learning experience.
Antivirus Flags Trojan In Official WordPress 6.6.1 Download
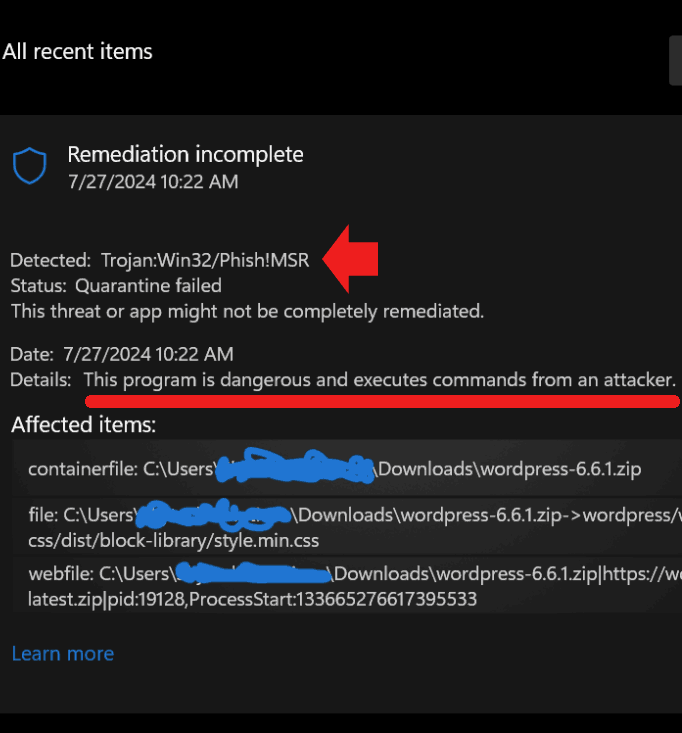
The first report was filed in the official WordPress.org help forums where a user reported that the native antivirus in Windows 11 (Windows Defender) flagged the WordPress zip file they had downloaded from WordPress contained a trojan.
This is the text of the original post:
“Windows Defender shows that the latest wordpress-6.6.1zip has Trojan:Win32/Phish!MSR virus when i try downloading from the official wp site
it shows the same virus notification when updating from within the WordPress dashboard of my site
Is this a false positive?”
They also posted screenshots of the trojan warning that listed the status as “Quarantine failed” and that WordPress zip file of version 6.6.1 “is dangerous and executes commands from an attacker.”
Screenshot Of Windows Defender Warning
Someone else affirmed that they were also having the same issue, noting that a string of code within one of the CSS files (style code that governs the look of a website, including colors) was the culprit that was triggering the warning.
They posted:
“I am experiencing the same issue. It seems to occur with the file \wp-includes\css\dist\block-library\style.min.css. It appears that a specific string in the CSS file is being detected as a Trojan virus. I would like to allow it, but I think I should wait for an official response before doing so. Is there anyone who can provide an official answer?”
Unexpected “Solution”
A false positive is generally a result that tests as positive when it’s not actually a positive for whatever is being tested for. WordPress users soon began to suspect that the Windows Defender trojan virus alert was a false positive.
An official WordPress GitHub ticket was filed where the cause was identified as an insecure URL (http versus https) that’s referenced from within the CSS style sheet. A URL is not commonly considered a part of a CSS file so that may be why Windows Defender flagged this specific CSS file as containing a trojan.
Here’s the part where things went off in an unexpected direction. Someone opened another WordPress GitHub ticket to document a proposed fix for the insecure URL, which should have been the end of the story but it ended up leading to a discovery about what was really going on.
The insecure URL that needed fixing was this one:
http://www.w3.org/2000/svg
So the person who opened the ticket updated the file with a version that contained a link to the HTTPS version which should have been the end of the story but for a nuance that was overlooked.
The (‘insecure’) URL is not a link to a source of files (and therefore not insecure) but rather an identifier that defines the scope of the Scalable Vector Graphics (SVG) language within XML.
So the problem ultimately ended up not being about something wrong with the code in WordPress 6.6.1 but rather an issue with Windows Defender that failed to properly identify an “XML namespace” instead of mistakenly flagging it as a URL linking to downloadable files.
Takeaway
The false positive trojan file alert by Windows Defender and subsequent discussion was a learning moment for many people (including myself!) about a relatively arcane bit of coding knowledge regarding the XML namespace for SVG files.
Read the original report:
Virus Issue :wordpress-6.6.1.zip shows a virus from windows defender
Featured Image by Shutterstock/Netpixi
